and secure intelligent IT overall management platform
In the continuous development of operation and maintenance security management is also facing serious challenges:
 Insufficient Resources IT growth is rapid and complex, familiarization with the IT business requires a process, and the accumulation of relevant talent is slow.
Insufficient Resources IT growth is rapid and complex, familiarization with the IT business requires a process, and the accumulation of relevant talent is slow. Information Silostool-oriented construction, the use of different security tools for different security issues, the data can not be effectively connected, security management .
Information Silostool-oriented construction, the use of different security tools for different security issues, the data can not be effectively connected, security management . Fragmentationwhere most organizations lack full visibility into their networks and users, lack a unified view of security and are vulnerable to untraceable threats.
Fragmentationwhere most organizations lack full visibility into their networks and users, lack a unified view of security and are vulnerable to untraceable threats. Slow Responsewith the help of various tools to respond, can not be automated across the tool disposal, detection and response passive, and slow implementation.
Slow Responsewith the help of various tools to respond, can not be automated across the tool disposal, detection and response passive, and slow implementation.
Based on the serious challenges faced, security management has also shifted from passive security tool-oriented construction to active management system-oriented construction, focusing on the integrity, efficiency and effectiveness of the security system and emphasizing deep defense and scalability.
InforCubeInforCube Security intelligent CA Platform (SiCAP) changes the management object from security risks to people and assets, takes data as the basis, intelligence as the support, service as the core, and scenario as the guide, breaks down the information silos, connects the isolated tools and resources, connects the data and integrates the capabilities, and shifts from fragmentation to integration, and builds a closed-loop management system through AI-driven, rapid detection, investigation, and automated response to realize flexible and adaptable full-scenario intelligent operation and maintenance security management.
 Untangle Management ObjectsSafety Risk Users and Assets
Untangle Management ObjectsSafety Risk Users and Assets Data Connectivity Capability IntegrationShards Incorporation
Data Connectivity Capability IntegrationShards Incorporation Building Closed-loop SystemMultisystem Secure Platform
Building Closed-loop SystemMultisystem Secure Platform

SiCAP is a platform product formed by combining the industry's emerging technology concepts of DevSecOps, AIOps and BiModalIT with information security, using ITSM 2.0 as the benchmark.;including Identity and Access Management(IAM)、Configuration Management Database(CMDB)、Integrated Monitoring and Management Platform(IMP)、Security Operations Comprehensive Audit(SOCA)、IT Service Management(ITSM)、Data Intelligence Analysis,six core product modules,Create a new generation of IT management platform for customers that is integrated, visualized, automated, secure and intelligent.
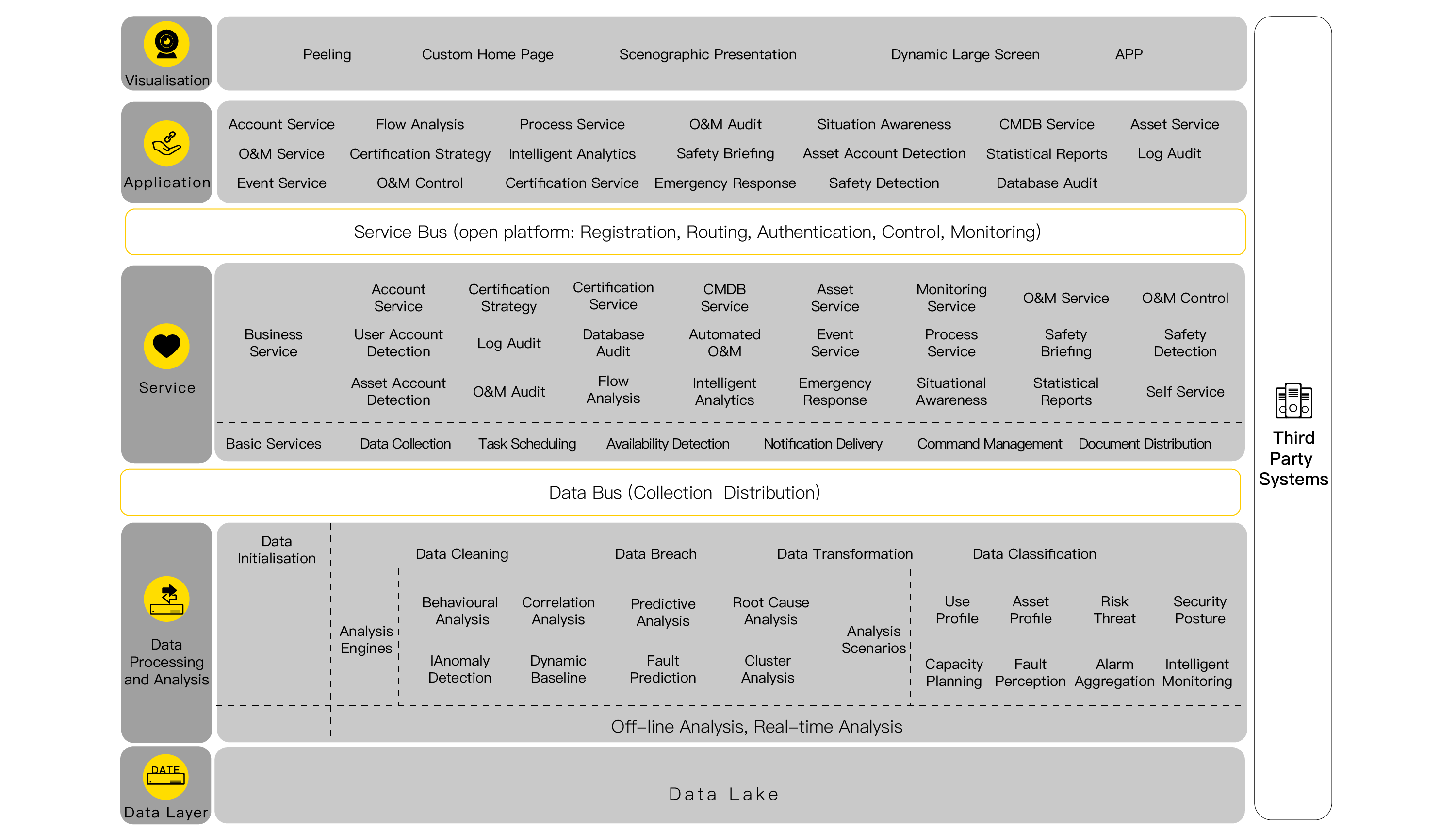
 IncorporationAround people and assets, to build a full picture of operation and maintenance security management, the openness and scalability of the platform to meet the individual needs of enterprises, easily tailored for the enterprise operation and maintenance, data and security of the trinity of IT operation and maintenance security management platform.
IncorporationAround people and assets, to build a full picture of operation and maintenance security management, the openness and scalability of the platform to meet the individual needs of enterprises, easily tailored for the enterprise operation and maintenance, data and security of the trinity of IT operation and maintenance security management platform. VisualizationBy comprehensively collecting and applying intelligent algorithms to comprehensively analyze the data in the entire IT infrastructure (from network, endpoints, users, cloud to applications), it achieves 360-degree visual management, aids in decision-making, and improves management effectiveness.
VisualizationBy comprehensively collecting and applying intelligent algorithms to comprehensively analyze the data in the entire IT infrastructure (from network, endpoints, users, cloud to applications), it achieves 360-degree visual management, aids in decision-making, and improves management effectiveness. AutomationFrom data collection to detection, investigation and response to processing, daily and auxiliary operations can be automated, standardized and processed by automation tools to reduce the risk of human operation, reduce the workload of operation and maintenance personnel, and improve the efficiency of operation and maintenance.
AutomationFrom data collection to detection, investigation and response to processing, daily and auxiliary operations can be automated, standardized and processed by automation tools to reduce the risk of human operation, reduce the workload of operation and maintenance personnel, and improve the efficiency of operation and maintenance. SecuritizationFrom the fine-grained control of user rights and hierarchical management of data to the security baseline and regular inspection of asset configuration, real-time monitoring and early warning of assets, and comprehensive control and auditing of operation and maintenance operations, it covers all aspects of security operation and maintenance, and fully complies with the security requirements of laws and regulations.
SecuritizationFrom the fine-grained control of user rights and hierarchical management of data to the security baseline and regular inspection of asset configuration, real-time monitoring and early warning of assets, and comprehensive control and auditing of operation and maintenance operations, it covers all aspects of security operation and maintenance, and fully complies with the security requirements of laws and regulations. IntelligentApplying big data technology and intelligent algorithms such as machine learning and pattern recognition, based on different business scenarios, it can deeply analyze user data, asset data, monitoring data, operation and maintenance data, log data, network traffic and other data within the system, carry out overall security protection, and provide more efficient and intelligent management.
IntelligentApplying big data technology and intelligent algorithms such as machine learning and pattern recognition, based on different business scenarios, it can deeply analyze user data, asset data, monitoring data, operation and maintenance data, log data, network traffic and other data within the system, carry out overall security protection, and provide more efficient and intelligent management.
此处放标题
内容暂无
电话:86-21-51905999
传真:86-21-51905959
邮编:201203
地址:上海市浦东新区张江高科技园区郭守敬路498号20号楼




